The GridDB Python client has been updated to now use the native GridDB Java interface with JPype and Apache Arrow. Prior to this release, the...
Automated Speech Dubbing Using GPT-4o Audio and Node.js
What This Blog is About Easy communication across languages is crucial in today’s interconnected world. Traditional translation and dubbing methods often fall short—they’re too slow,...
Stress Detection using Machine Learning & GridDB
Stress significantly affects individuals' well-being, productivity, and overall quality of life. Understanding and predicting stress levels can help take proactive measures to mitigate its adverse...
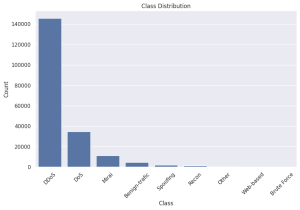
IoT Intrusion Detection
Intrusions refer to unauthorized activities that exploit vulnerabilities in IoT devices, which can compromise sensitive data or disrupt essential services. Detecting these intrusions is crucial...